As per the Proximity Cloud Concepts section of this document, our customers can split their Availability Zone into different Security Zones. One reason for doing this is to be able to offer share the same Availability Zone between multiple clients. These clients will share the same Availability Zone but can have their Compute setup in a distinct Security Zone for each customer. An example use case for doing this is for an Exchange to split up an Availability Zone between different exchange members.
Another possible use of a Security Zone is to create a ‘DMZ’ Security Zone which is open to inbound connections from the internet for certain clearly defined applications. Applications in the Trusted Zone would have no direct internet access permitted to them (although they may be allowed outbound access to the internet, for example to access external patch repositories - this access would only be possible if an application in the Trusted Zone initiated the connection). For a more detailed description of the Proximity Cloud networking, please see the Technical Deployment Guide for Proximity Cloud & Exchange Cloud.
Definitions
A Security Zone is a part of the physical network for the Availability Zone that is logically separated from the other networks. Communication between Security Zone will only be possible by connecting through a firewall. For those familiar with network terminology, VRF (Virtual Router Forwarding) separation is used to achieve this network separation. This means that each network segment has its own layer 3 routing table, and that routing between network segments is not possible without explicit configuration. A Security Zone will be made up of one or more Networks.
A Network (in Proximity Cloud terms) is a Virtual Local Area Network (VLAN). This means that hosts within the same network can communicate directly with each other, without extra configuration, as long as they are configured with the correct networking details.
For Proximity Cloud, we make the simplifying assumption that each VLAN will have one and only one IP prefix assigned to it. In network terms, both layer 2 and layer 3 concepts are embodied by the same object in the Portal. See the Technical Deployment Guide for Proximity Cloud & Exchange Cloud for more information about Proximity Cloud network concepts and topology.
Example Usage
An Exchange Cloud user may split their Availability Zone between multiple clients.
Each client would have its own Security Zone. This ensures that these clients cannot communicate directly with each other.
A client may have a Production network and a Test network. The Production network would be used for trading and the Test network would be used for conformance testing, testing new application changes, etc. Keeping these hosts in different networks ensures that an application misconfiguration on the Test network (for example, a broadcast storm) does not impact applications on the Production network.
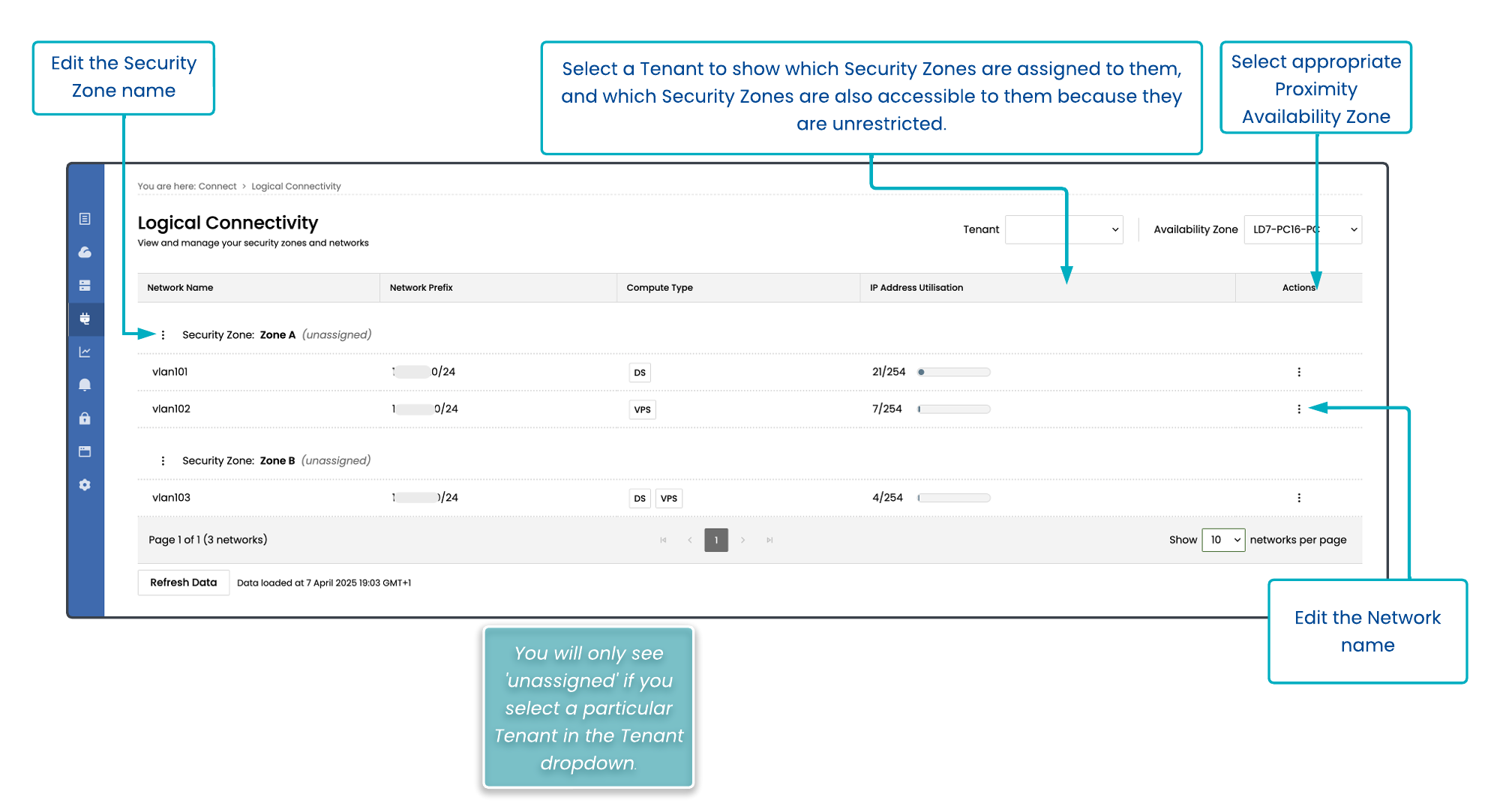
Using Logical Connectivity to manage your Networks
The Logical Connectivity page provides an overview of the networking for each of your Proximity Availability Zones.
To access the Logical Connectivity page, go to Connect > Logical Connectivity.
This page allows Administrators to rename Networks and Security Zones.
You can also apply an optional filter for a given tenant, to see which individual Security Zones are assigned specifically to that tenant. All other Security Zones will show with unrestricted next to their names.
The Compute Type will show whether a network is reserved for Dedicated Servers or Virtual Private Servers. Some networks can have both types of compute assigned to them.
The IP Address Utilisation column shows you the available IP addresses that are remaining within that network.
If there are no more IP addresses available within a particular network, you will not be able to deploy any compute items until some address space is freed up. Raise a Support ticket if you need advice on this.
The networks/{availability_zone_uuid} and security-zones API endpoints provide information about the Proximity Cloud network setup.
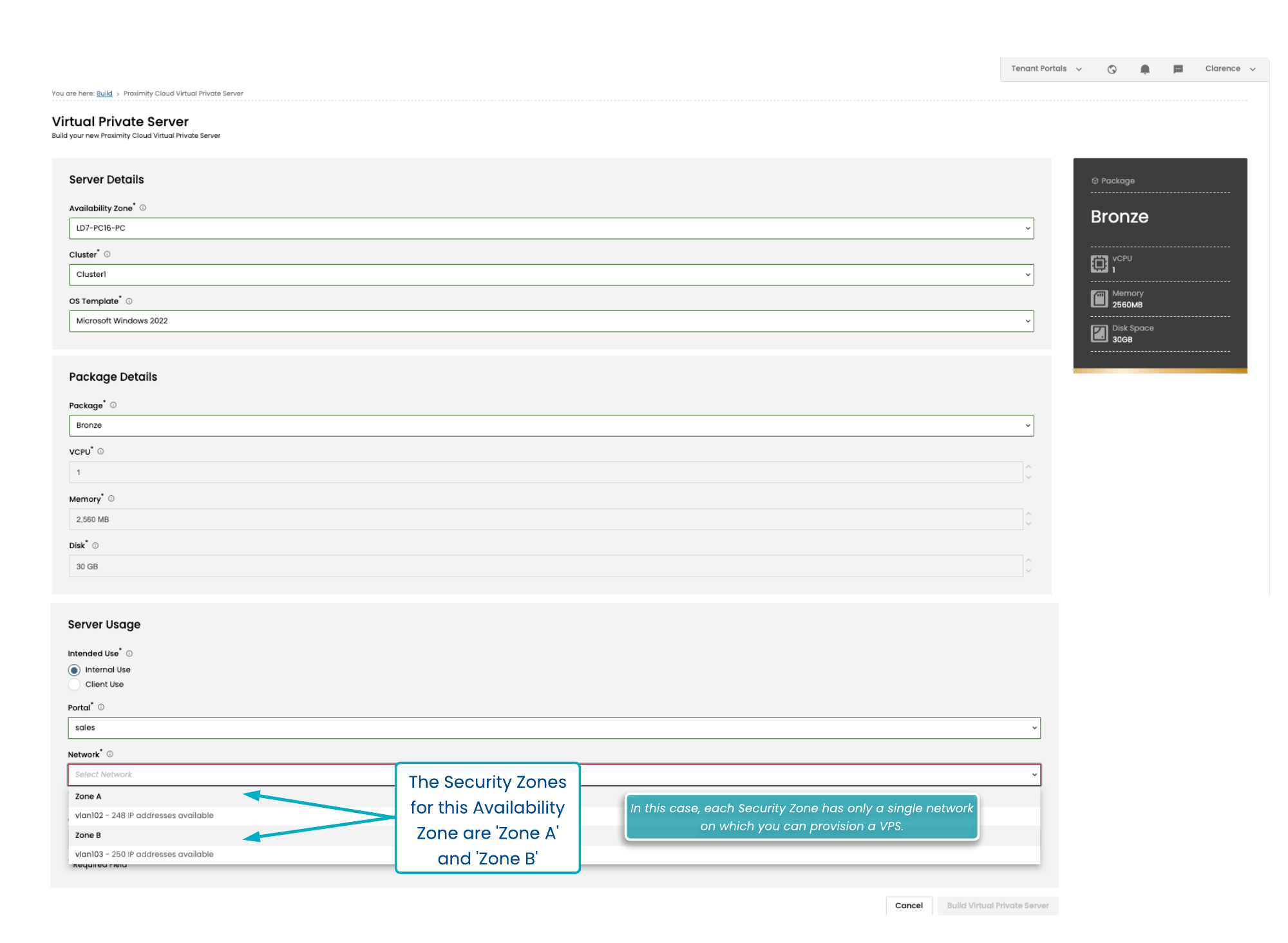
Deploying a Compute Item to a Particular Network
See Building Compute for full details of the build options.
One of the options which is mandatory is the choice of network that the DS or VPS will be assigned to. You will see all of the available Networks grouped by Security Zone.
Choose the appropriate option and the appropriate network change will be included in the build order for that host.
VPS Network Separation
Note that networking for VPS can have extra protections in place at the hypervisor layer to prevent hosts from communicating with each other, even if the VPSs are assigned to the same network. Please consult your Beeks technical contact if you are not sure of what communication is possible between different VPSs.
Other Network Actions
The creation, editing (other than renaming) and removal of Security Zones and Networks is outside the scope of the current document, and can be done in consultation with your Beeks technical contact.
Editing the Network or Security Zone that a Compute Item is assigned to will be done in consultation with your Beeks technical contact, as the network change and server change need to be coordinated together - usually the subnet mask and gateway of the host will need to also be updated to reflect the new networking details. This co-ordination activity can be kicked off by a Support ticket raised in the Portal.